


Researchers Demonstrate How MCP Prompt Injection Can Be Used for Both Attack and Defense
Read More As the field of artificial intelligence (AI) continues to evolve at a rapid pace, new research has found how techniques that render the Model Context Protocol (MCP) susceptible to prompt injection attacks could be used to develop security tooling or identify...![[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats ](https://cubexgroup.com/wp-content/uploads/2025/04/webinar-play-I8mNBR.jpg)
[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats
Read More How Many Gaps Are Hiding in Your Identity System? It’s not just about logins anymore. Today’s attackers don’t need to “hack” in—they can trick their way in. Deepfakes, impersonation scams, and AI-powered social engineering are helping them bypass traditional...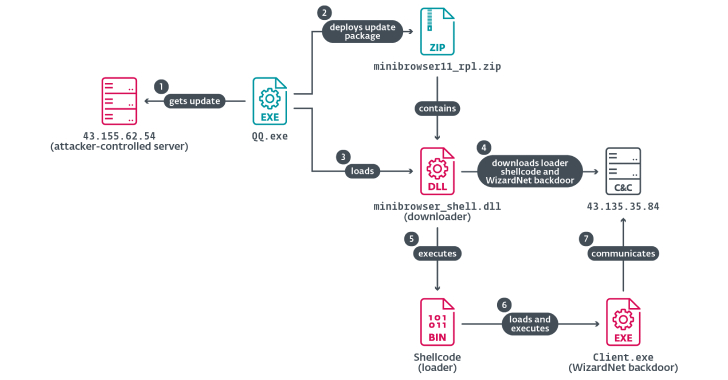
Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool
Read More A China-aligned advanced persistent threat (APT) group called TheWizards has been linked to a lateral movement tool called Spellbinder that can facilitate adversary-in-the-middle (AitM) attacks. “Spellbinder enables adversary-in-the-middle (AitM)...