

How Breaches Start: Breaking Down 5 Real Vulns
Read More Not every security vulnerability is high risk on its own – but in the hands of an advanced attacker, even small weaknesses can escalate into major breaches. These five real vulnerabilities, uncovered by Intruder’s bug-hunting team, reveal how attackers...
Earth Kurma Targets Southeast Asia With Rootkits and Cloud-Based Data Theft Tools
Read More Government and telecommunications sectors in Southeast Asia have become the target of a “sophisticated” campaign undertaken by a new advanced persistent threat (APT) group called Earth Kurma since June 2024. The attacks, per Trend Micro, have...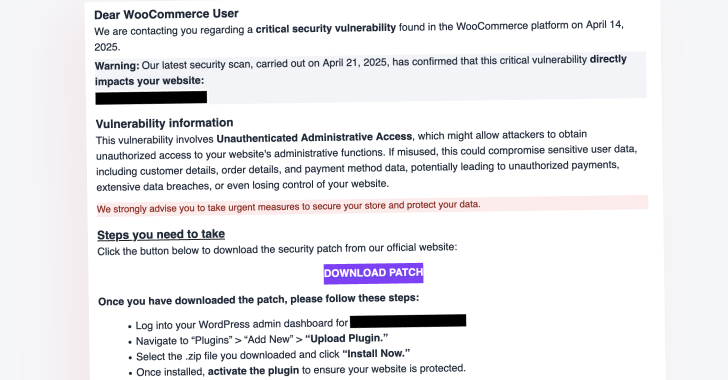
WooCommerce Users Targeted by Fake Patch Phishing Campaign Deploying Site Backdoors
Read More Cybersecurity researchers are warning about a large-scale phishing campaign targeting WooCommerce users with a fake security alert urging them to download a “critical patch” but deploy a backdoor instead. WordPress security company Patchstack...