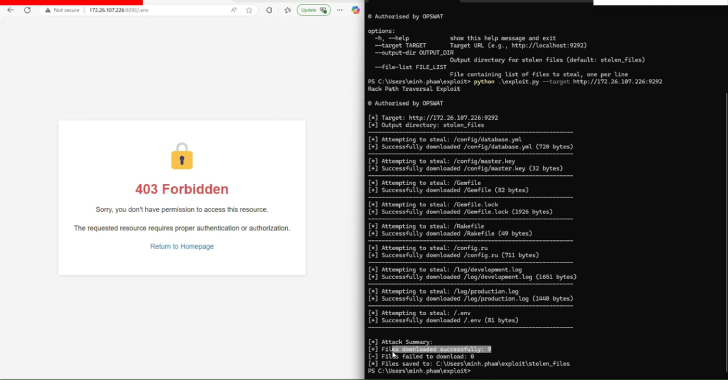

DslogdRAT Malware Deployed via Ivanti ICS Zero-Day CVE-2025-0282 in Japan Attacks
Read More Cybersecurity researchers are warning about a new malware called DslogdRAT that’s installed following the exploitation of a now-patched security flaw in Ivanti Connect Secure (ICS). The malware, along with a web shell, were “installed by...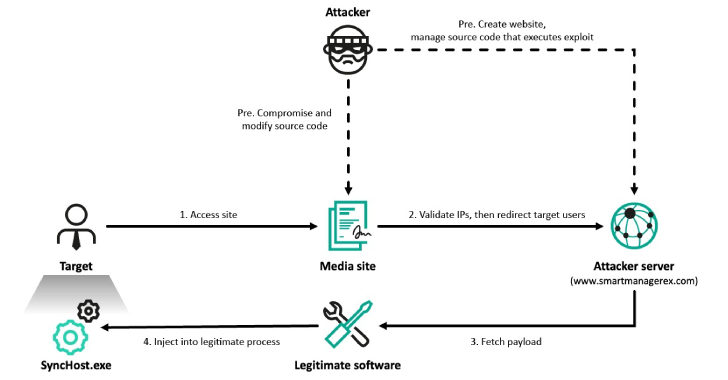
Lazarus Hits 6 South Korean Firms via Cross EX, Innorix Flaws and ThreatNeedle Malware
Read More At least six organizations in South Korea have been targeted by the prolific North Korea-linked Lazarus Group as part of a campaign dubbed Operation SyncHole. The activity targeted South Korea’s software, IT, financial, semiconductor manufacturing, and...
Linux io_uring PoC Rootkit Bypasses System Call-Based Threat Detection Tools
Read More Cybersecurity researchers have demonstrated a proof-of-concept (PoC) rootkit dubbed Curing that leverages a Linux asynchronous I/O mechanism called io_uring to bypass traditional system call monitoring. This causes a “major blind spot in Linux runtime...