

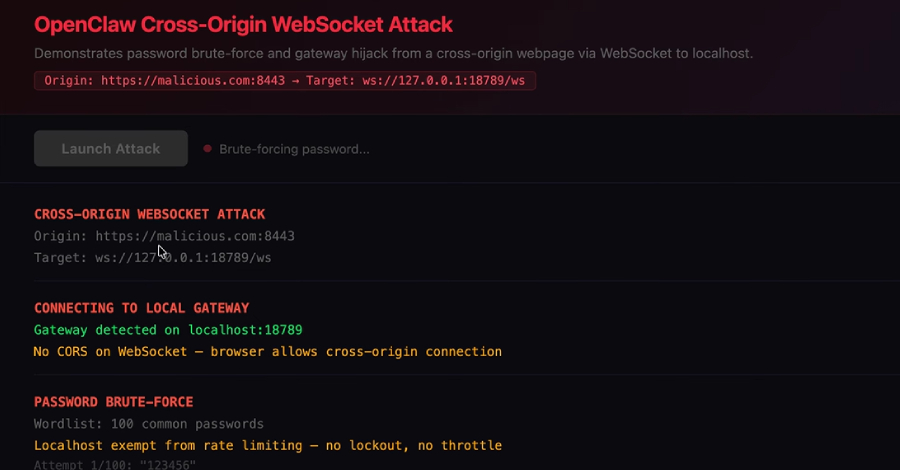
ClawJacked Flaw Lets Malicious Sites Hijack Local OpenClaw AI Agents via WebSocket
Read More OpenClaw has fixed a high-severity security issue that, if successfully exploited, could have allowed a malicious website to connect to a locally running artificial intelligence (AI) agent and take over control. “Our vulnerability lives in the core...
Thousands of Public Google Cloud API Keys Exposed with Gemini Access After API Enablement
Read More New research has found that Google Cloud API keys, typically designated as project identifiers for billing purposes, could be abused to authenticate to sensitive Gemini endpoints and access private data. The findings come from Truffle Security, which...
Pentagon Designates Anthropic Supply Chain Risk Over AI Military Dispute
Read More Anthropic on Friday hit back after U.S. Secretary of Defense Pete Hegseth directed the Pentagon to designate the artificial intelligence (AI) upstart as a “supply chain risk.” “This action follows months of negotiations that reached an...